
Latest Insights
Explore our blog for the latest trends, tips, tutorials and technologies that are shaping the future of software development.

An In-Depth Look at the Adobe Premiere Pro Editing Tools
The toolbox contains common tools used for editing clips in the timeline. Click on any of the buttons or use the…
Why developer choose React JS
Craze and trends of the react js in 2022, Why developer choose React JS for web development…
Points to Learn from Your Competitors about Beta Testing
Currently there is a lot of competition in the market. As everybody’s

How To Setup SSH key in Windows
In this article, I show you how to set up SSH in

Importance of Employee Motivation
Importance Motivation allows management to attain its goals. Without motivation, It’s…
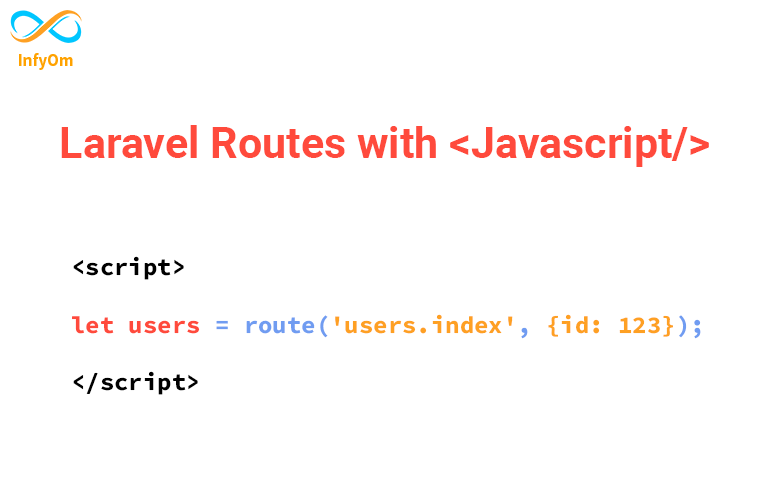
How to use laravel routes with Javascript / JQuery ?
Generally, we can use laravel routes into its blade files, but what
Top 5 web design trends that will shape the future
Custom web design can be the difference between a mediocre website and an awesome…

How to Start and Stop Jobscheduler in Android
Android apps will work in the background (Android Background Service) mode to
User Acceptance Testing Tips for Testers
User Acceptance Technique is widely used for its efficiency and effectiveness.If…